PDEC (Personal Data Ecosystem Consortium) is a not-for-profit trade association with members around the world. We exist to activate and broaden the Personal Data Ecosystem. An Ecosystem that centers on people and their data, that enables organisations to make person-centered data logistics a reality.
Core Principles – What we stand for
| ❶ | Protecting People and their rights – empowerment, personal control over personal data and identity and transparency about where and how it is used. | |
| ❷ | Protecting Organizations and their rights in whatever role they undertake – ensuring there is a basis for reaching agreement on shared challenges and ensuring transparency and accountability regarding data that they retain, transmit or exchange about people. |
|
| ❸ | Interoperability across open diverse ecosystems with diverse business models. | |
| ❹ | The creation of successful business models to deliver return on investment justifications and monetization strategies for companies operating in the personal data ecosystem. |
What our members say:
“Our PDEC membership made us feel part of an industry. By joining, we immediately felt as we had a focal point for remaining current with industry trends, breaking news, and industry associations.”
– Mark L. Black, Origin Incorporated
“PDEC is THE trade organization for any company that wants to be seriously involved in the personal data or personal cloud industry. No other organization has the unique DNA needed to organize companies who are all committed to putting the user first.”
– Drummond Reed, Respect Network
“Kaliya brought a breath of fresh air to the identity conversations in New Zealand – forward thinking but not stratospheric, optimistic but not unrealistic – and above all, provoked thought and discussion long after she departed our shores.”
— Colin Wallis, Executive Director, Kantara and Identity Rockstar of New Zealan
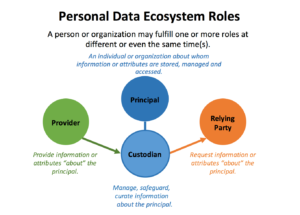
PDEC definitions of Personal Data Ecosystem Roles:
- Principal – The principal is a person or organization that is identified by, described by or related to, information or attributes that can be stored about them and exchanged with other interested parties. The principal is a primary active participation role, not simply defined as subject (as defined in data protection legislation relating to individuals who are the subject of a process or data)
- Providers – Those organizations who generate, validate, create, or certify information or attributes relating to principals that other roles within the ecosystem may wish to collect, protect, curate, or access and make use of.
- Custodian – Those organizations that are not interested in the actual information itself but rather provide services and solutions for the secure collection, transmission, exchange, storage, curation, management of the data on behalf principals. In general, it is by the explicit delegation of a principal that a custodian is empowered to operate on their behalf.
- Relying Party – An organization, service or solution that requests, consumes or relies on data from others about or related to principals.